Security Management Software "SecureLock Manager2" and Installation USB memory device
RUF2-HSC-MGR
The combination of the software and installation device brings you easy setup for ideal security management.
Enables administrators to design ideal security policies

RUF2-HSC-MGR allows administrators to centralize management of compatible USB memory drives. It provides a secure environment that is accessible only to administrators and users, with administrators having free access through the master key file. This allows administrators to access data on compatible products and provides them with a variety of settings.
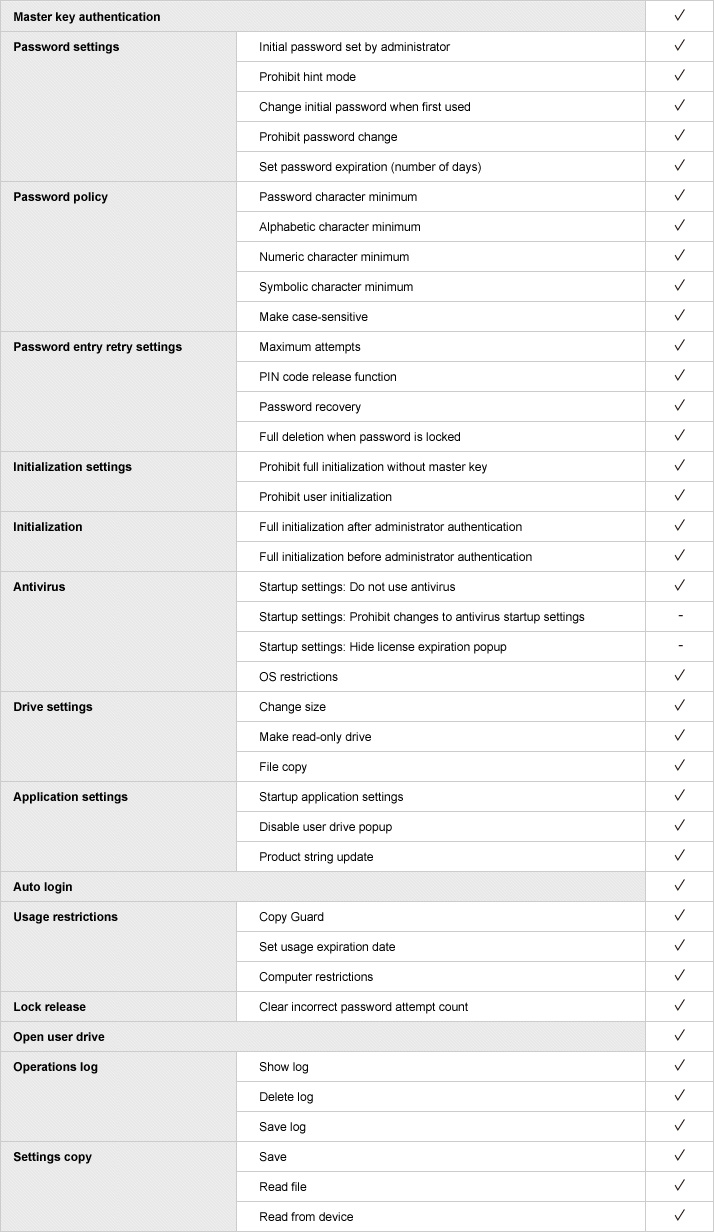
Enables authentication with individual master key files
SecureLock Manager 2 software allows authentication of multiple compatible devices using their separate master key files.
This option is recommended when different settings for multiple compatible devices are desired.
* A master key file is a key used to authenticate compatible devices. It is used by system administrators to access data stored on these devices, set passwords, and perform other tasks.
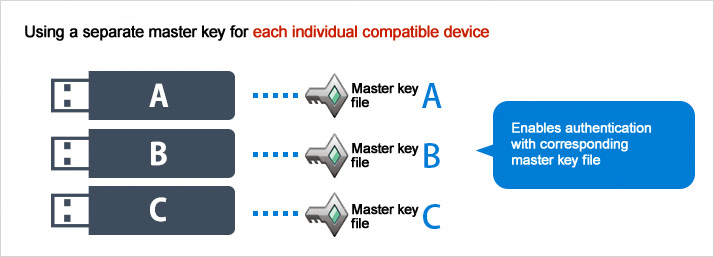
Manage multiple groups with a single master key
SecureLock Manager 2 software allows a single common master key file to be shared by large numbers of compatible devices.
Managing numerous devices with a single master key file vastly reduces the administrator's operational workload.
* A master key file is a key used to authenticate compatible devices, used by system administrators to access data stored on these devices, set passwords, and perform other tasks.
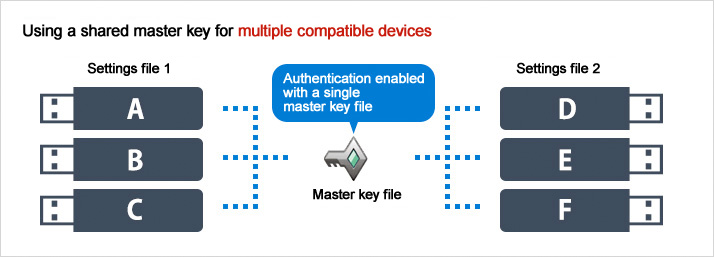
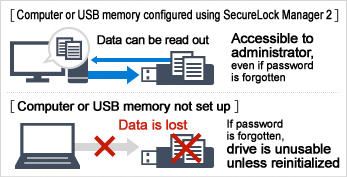
No worries about forgotten passwords—avoids the risk of critical data loss
Many conventional secure drive products require a full reinitialization when a user forgets the password to unlock the drive. However, system administrators can use the master key file to access the data on the drive, even if the user happens to forget the user password.
This allows the administrator not only to read the stored data, but to reset the user password as well. This application of the management software is also recommended as a way to prevent loss of critical data.
Authentication is easy, settings are simple—no cumbersome details needed
Authenticating with the master key file allows you to read and write data to and from compatible devices and make settings to these devices. There is no need for additional information such as user-set passwords or other settings beside those made by the system administrator, which reduces the system administrator's workload.
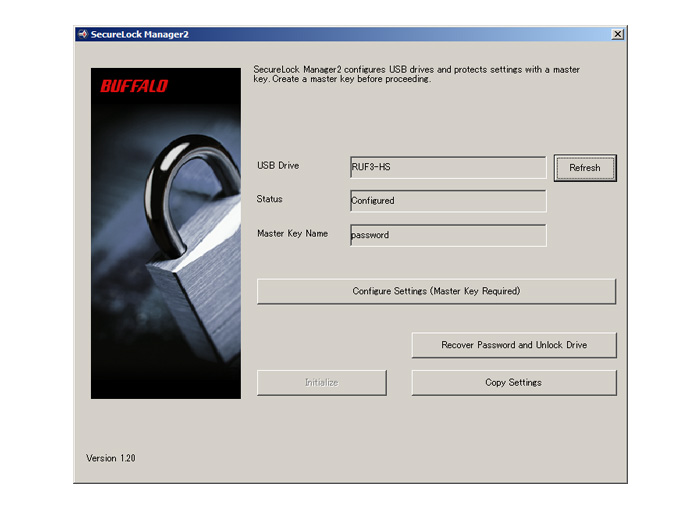
Enhanced security to match usage conditions - manage passwords with multiple settings
SecureLock Manager 2 software offers numerous password-related settings, including a setting determining whether the initial password is set by the administrator or the user, conditions for entering the user-set password, the number of failed password entries allowed before the drive is locked down, and more.
In addition, while many security products must be completely reinitialized if the user happens to forget the password, SecureLock Manager 2 software allows the password to be reset while leaving the data on the drive untouched.
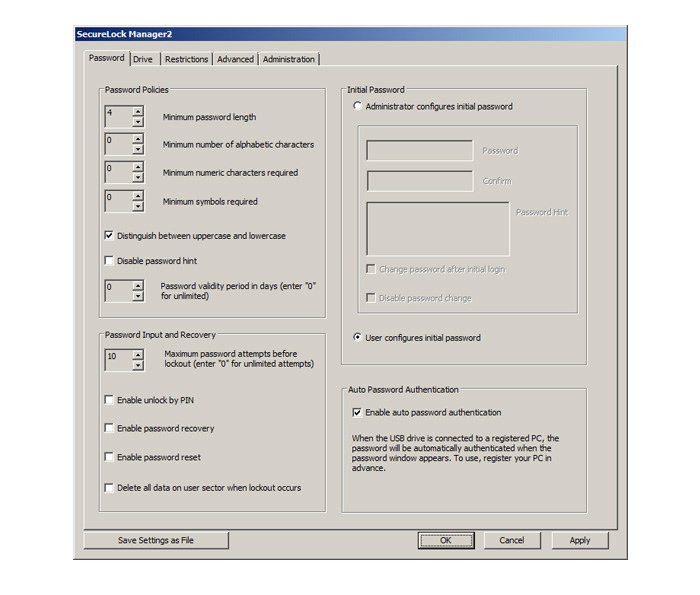
Password expiration term
This function allows businesses, government agencies, and other organizations to have their users make mandatory or periodic changes in the password, in line with the organization's particular security policies. Requiring new passwords after a preset number of days and regularly changing (updating) to other newly-selected passwords helps enhance security and prevent unauthorized access.
The software prohibits use of any of the eight most recent passwords.
PIN code release
When the number of failed password entries exceeds the preset limit on of retries, the compatible product is then locked and cannot be accessed using password authentication. When this occurs, the lock can still be released remotely with an administrator-issued PIN code (up to nine characters long).
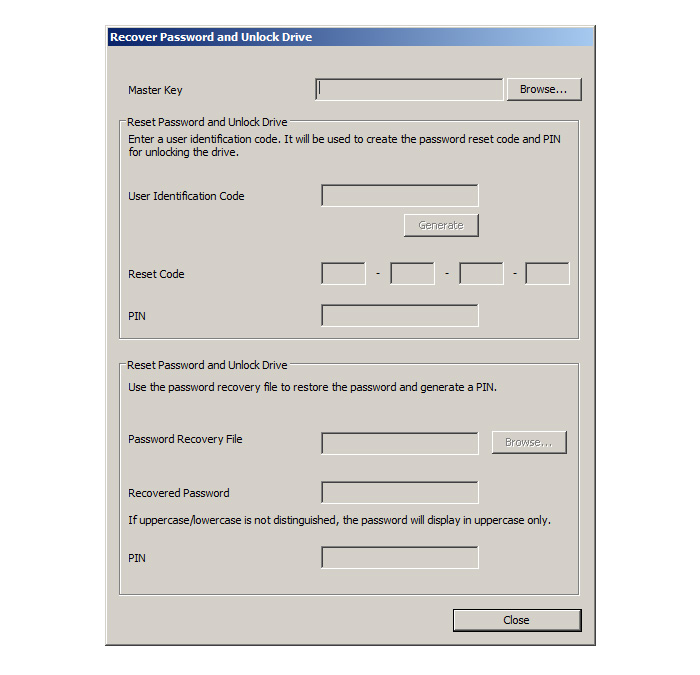
Password recovery
This function allows a current user password to be restored from a user file acquired by email or other means. The PIN code is also generated simultaneously.
Password reset
User passwords can be reset remotely with a 16-character reset code issued by the administrator.
Completely deleting data on a user's drive when the password is locked
Not only can the password be locked when the number of failed password entries exceeds the preset limit, the drive can also be set to simultaneously delete the data. In comparison to conventional lock-only options, this provides even more robust protection against unauthorized access by third parties.
Release the lock set due to failed password attempts
If password authentication is locked after the user enters the
password incorrectly, the product can be returned and the
lock released. This is a reassuring option when the drive
becomes locked in a remote location where the drive cannot be handed directly to an administrator. The lock can be released simply and easily, even from a remote location, just by communicating the user's ID code and the administrator's lock release PIN code over the phone or through other means. Alternatively, mandatory access can be used to get data from the user's drive, even without knowledge of the user's password.
Adjusting the capacity of each drive
USB memory comprises an administrator drive and user drive. The administrator drive is a dedicated read-only drive that is used for storing user password input and authentication tools, software and tools delivered by administrators to users, and other content. The user drive is where the user can freely store files and other data. Access to this data requires authentication, and all stored data undergoes forced encryption, for greater assurance in the use of the data.
The size of these drives can be modified, and files can be written to the administrator drive.
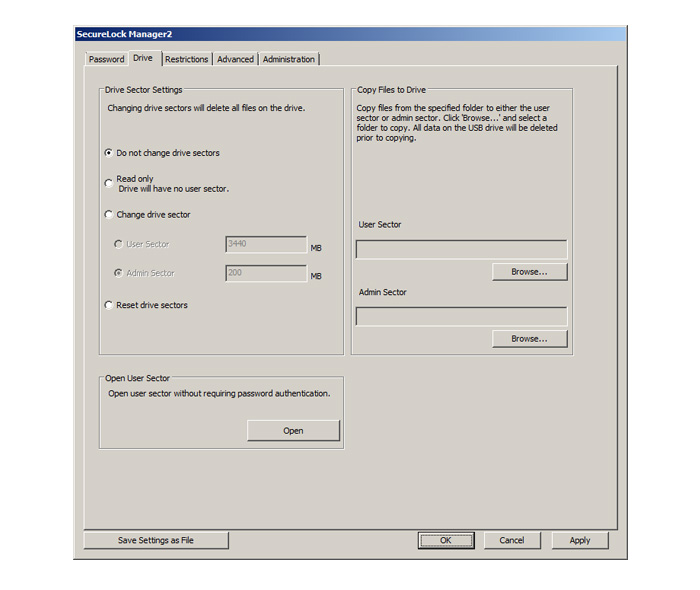
* As the administrator drive can be accessed without authorization, it is not suitable for saving highly confidential information.
Examples of modifying the drive size
Increasing the size of the administrator drive
If you need to put a large file on a read-only administrator drive, you can designate a drive whose size can be modified as an administrator drive, and then increase the size. This not only increases the size of the drive, it also allows use of the file copy function to copy the designated file to the read-only administrator drive. In addition, you can start up the program copied to the administrator drive by jointly using the settings for the application launched after password or fingerprint authentication.
Reducing the size of a user drive
You can reduce the size of a user drive when is not desirable to have the user carry large amounts of data. After designating a drive whose size can be modified as administrator drive, you can fix the user drive size to the specified size, even with drives with 2 GB, 4 GB, 8 GB or other multiples.
Other convenient settings
Read-only settings
Drives can be distributed as read-only USB memory, making them suitable for software distribution.
Additionally, since data cannot be written to these drives, users do not need to worry about the threat of viruses.
Set multiple devices easily
USB memory password settings and drive settings can be saved to a settings file, and these saved settings can then be read and copied to another product of the same type.
This allows the same settings to be saved on multiple USB memory products, which reduces the administrator's burden in making these settings.
Full reset to default settings
You can delete all password settings data and all data in the USB memory and return the device to the factory default settings.
* The antivirus activation date cannot be deleted.
Limit use on computers other than those specified
Select the following functions in line with the particular usage conditions.
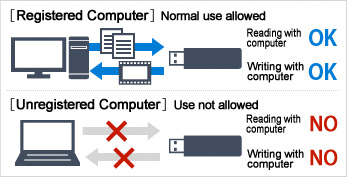
Copy Guard
The USB drive can be used normally with specified computers, but other computers are prohibited from copying content from the USB drive to the computer or printing out data contained in the USB memory.
Data can be overwritten. Additionally, no installation is required for use of the software, even for user authorization.
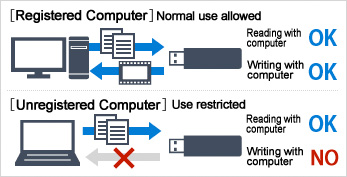
Prohibited Use
This permits use of the USB memory only with specified computers. The USB memory cannot be used with other computers, even when connected to these computers.
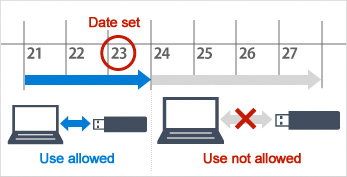
Setting usage restrictions
You limit the period users can use the USB memory by setting an expiration date after which use is not allowed. The software can also be set to delete data once the period is past.
* This feature can be used with either "Copy Guard" or "Prohibited Use"
Copy Guard details
-Use of Explorer to copy files on a user drive to a computer is prohibited.
-Files on a user drive cannot be saved to a computer while any application (e.g., Microsoft Word) is open. Files can be saved only to the user drive.
-Files on a user drive cannot be saved to a computer by opening the file on the user drive then copying and pasting it to the computer.
-Screen shots are not permitted while Copy Guard is enabled.
-Files on a user drive cannot be opened and printed while Copy Guard is enabled (but may be allowed with certain settings).
-The Internet cannot be accessed while Copy Guard is enabled (but may be allowed with certain settings).
Log function allows administrators to track operations
Changes in settings and other specified operations on USB drives managed with SecureLock Manager 2 software are automatically saved to the USB memory as operations log data. Connecting the drive to an administrator's computer allows the administrator to check how the drive has been used. The log indicates the number, time, name of the computer, and operation, listed from the most recent entry. The log holds up to a maximum or 10,000 entries (however, mistaken passwords use two entries; therefore, the actual number of log entries is slightly less than 10,000).
* Indicates maximum log entries for the RUF3-HS Series, RUF3-HSTV Series, RUF3-HSTV3 Series, and RUF3-HSTV5 Series.
Acquire file access logs
In addition to the operations log enabling confirmation of
actions involving the USB memory, the software can also provide a file access log that allows the administrator to see how any particular file has been accessed. Click the SecureLock Manager 2 software "Drive Settings" tab and
place a check in the "File Access Log Function" check box to activate the function.
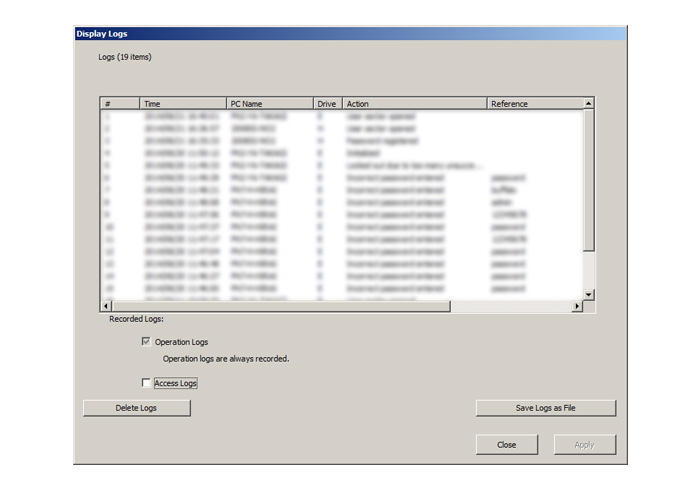
* Maximum 10,000 log entries for the RUF3-HS Series, RUF3-HSTV Series, RUF3-HSTV3 Series, and RUF3-HSTV5 Series. Depending on log content, the maximum number of log entries may be less than 10,000.
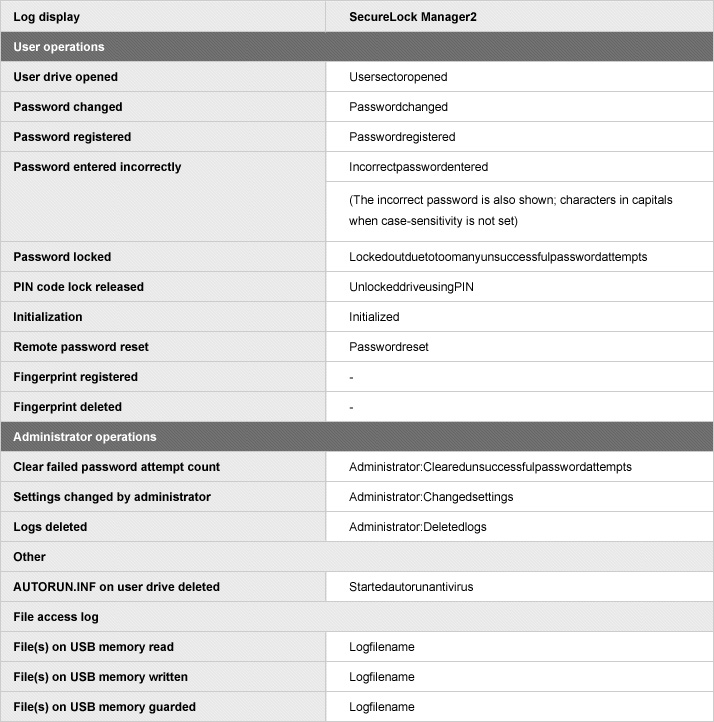
Log List
Supports "Product String Update" function reinforces internal controls
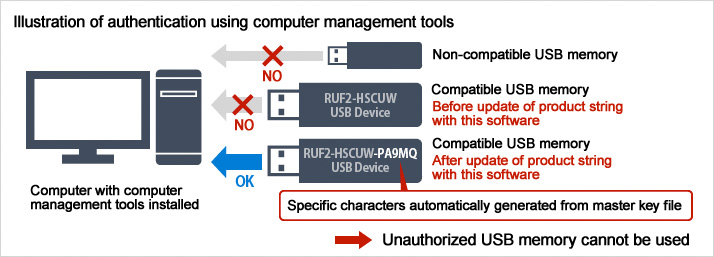
This feature links the software to commercial computer management tools with functions that authenticate USB memory according to the product string, creating an environment in which only USB drives allowed by the administrator can be used.
The Product String Update function included with SecureLock Manager 2 software adds a character string automatically generated from the master key file to the product string. This allows the software to distinguish USB drives with product strings that do not include the automatically generated character string, allowing use only of permitted USB memory.
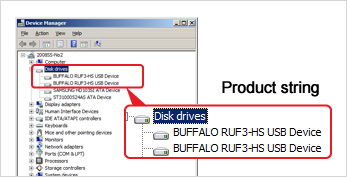
What is a product string?
A product string is a "name" used in managing devices (products) connected to Windows systems. These strings can be confirmed in the device manager screen. Use of this software in combination with compatible USB memory permits rewriting of product strings that cannot normally be modified, allowing the strings to be used as identifiers during authentication.
What are computer management tools?
Computer management tools are security software installed with the aim of preventing unauthorized access to businesses' computers and reinforcing internal controls. Some programs sold by various security software makers include functions used for viewing product strings.
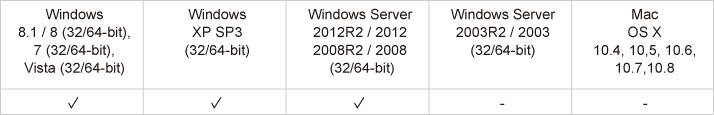
OS Support
Feature List